Dynamic Code Analysis using Owasp zap tool
Dynamic analysis is the testing and evaluation of a program by executing data in real-time. The objective is to find security errors in a program while it is running. Owasp zap dynamic analysis testing empowers companies to identify and re-mediate security issues in their running web applications before hackers can exploit them. By dynamically testing web applications in a run-time environment, Owasp zap inspects applications the same way a hacker would attack them – providing the most accurate and actionable vulnerability detection available.
Dynamic code analysis advantages:
- It identifies vulnerabilities in a run time environment.
- Automated tools provide flexibility on what to scan for.
- It allows for analysis of applications in which you do not have access to the actual code.
- It identifies vulnerabilities that might have been false negatives in the static code analysis.
- It permits you to validate static code analysis findings.
- It can be conducted against any application.
Dynamic code analysis limitations:
- Automated tools provide a false sense of security that everything is being addressed.
- Automated tools produce false positives and false negatives.
- Automated tools are only as good as the rules they are using to scan with.
- There are not enough trained personnel to thoroughly conduct dynamic code analysis [as with static analysis].
- It is more difficult to trace the vulnerability back to the exact location in the code, taking longer to fix the problem.
OWASP Bricks - Tuivai
Php project "OWASP Bricks - Tuivai" can be run on wamp server. If wamp server already configured just extract the above named zip files to www directory inside the wamp.
Bricks database have to be created using
phpmyadmin page. DB name will be bricks, Check for the below link for
additional information.
Owasp Zap Tool
Download Owasp zap tool using following link.
After installing owasp zap on windows machine then it should be configured before run a scan.
Close all active Firefox browser sessions ZAP tool -> Tools Menu -> Options -> Local Proxy -> Change Address = 127.0.0.1 Port = 8080. Mozilla browser -> Tools Menu -> Options -> Advanced tab -> Network -> Settings -> Select Manual Proxy configuration:- HTTP Proxy = 127.0.0.1 Port = 8080.
Now try to connect to your application using your browser.
If you can’t connect to it then check your proxy settings again. You will need to check your browser’s proxy settings, and ZAP’s proxy settings. It’s also worth checking that the application that you are trying to test is running.
When you have successfully connected to your application you will see one or more lines in ZAP’s Sites and History tabs.
Note that most of ZAP’s tabs provide additional functionality that could be accessed via ‘right click’ menus.
Right click on the HTML -> Attack -> Active scan
ZAP will perform active scan on all the pages and display the results.
In this case localhost/bricks didn't appear on the sites list, so I manually gave the path and start the attack. First it will run the spiral and then start the actual attack.
I selected following vulnerabilities to repair as examples.
- Directory Browsing-medium
- XSS - critical
- SQL injection -critical
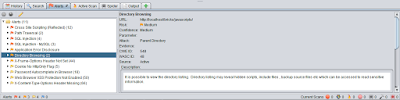
Directory Browsing
As the countermeasure added .htaccess file and configured. It is a server configuration file and configure apache server on runtime according to the given instructions.
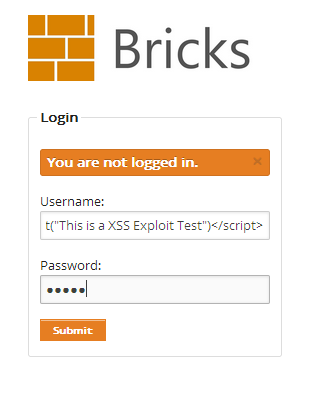
XSS
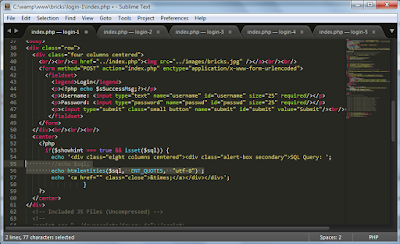
The XSS vulnerabilities are exploited using a simple javascript code.SQL Injection
Following images will show how vulnerability exploited and countermeasures added.Final vulnerability scan report shows following results and clearly shows which vulnerabilities were fixed during bug fixing.
This concludes the blogpost about Dynamic Code Analysis using owasp zap software. Following link has all the repositories used for above activity.
https://github.com/ara123/SSE_assignment_2
https://github.com/ara123/SSE_assignment_2















Pragmatic Play launches new slot in Asia - JTM Hub
ReplyDeletePragmatic Play, the world's leading content 구리 출장샵 provider to 부천 출장안마 the gaming industry, today announced that 군포 출장마사지 it 남원 출장마사지 has entered the 대구광역 출장안마 Asian market in a