Static Code Analysis
Static
Code Analysis (also known as Source Code Analysis) is usually performed as part
of a Code Review (also known as white-box testing) and is carried out at the
Implementation phase of a Security Development Life-cycle (SDLc). Static Code
Analysis commonly refers to the running of Static Code Analysis tools that
attempt to highlight possible vulnerabilities within 'static' (non-running)
source code by using techniques such as Taint Analysis and Data Flow Analysis.
Ideally, such
tools would automatically find security flaws with a high degree of confidence
that what is found is indeed a flaw. However, this is beyond the state of the
art for many types of application security flaws. Thus, such tools frequently
serve as aids for an analyst to help them zero in on security relevant portions
of code so they can find flaws more efficiently, rather than a tool that simply
finds flaws automatically.
Some tools
are starting to move into the Integrated Development Environment (IDE). For the
types of problems that can be detected during the software development phase
itself, this is a powerful phase within the development life-cycle to employ
such tools, as it provides immediate feedback to the developer on issues they
might be introducing into the code during code development itself. This
immediate feedback is very useful as compared to finding vulnerabilities much
later in the development cycle.
Techniques
- Data Flow Analysis
- Control Flow Graph (CFG)
- Taint Analysis
- Lexical Analysis
https://www.owasp.org/index.php/Static_Code_Analysis
How to setup the tools.
- Tool used for static code analysis - "rips-0.55"
- Vulnerable web application used for demonstration - "Before_OWASP Bricks - Tuivai"
- Web application after fixing several bugs - "After_bricks"
- Generated reports using the tool RIPS - "Generated Reports"
Using above link all the tools and samples which are relevant to this blog post can be downloaded.
Both tools "OWASP Bricks - Tuivai" & "rips-0.55" can be run on wamp server. If wamp server already configured just extract the above named zip files to www directory inside the wamp.
Now "rips-0.55" is ready but for Bricks, database have to be created using phpmyadmin page. DB name will be bricks, Check for the below link for additional information.
Bricks Homepage
RIPS Homepage
This tool contains very simple user interface with several options. Below link will help with further details about the tool
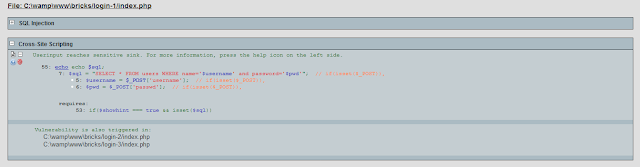
Run the vulnerability scanner on bricks
- XSS
Within few seconds it will prompt the results as in the above image.
Then I decided to try with the following vulnerability first. It is a XSS vulnerability.
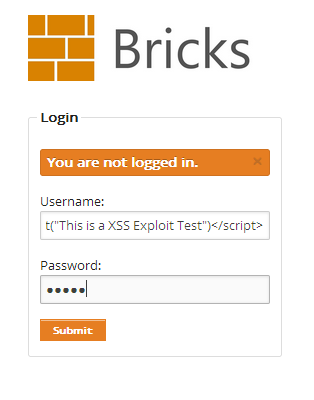
Exploit the XSS vulnerability
Simply input the following javascript command into any textbox included in the vulnerable page and click submit button. It will give the following output because it is vulnerable to XSS.
<script>alert("This is a XSS Exploit Test")</script>
Fixing the XSS vulnerability
Using htmlentities() function the problem was fixed.
Using the same method I fixed all the xss bugs in the project.
2. SQL Injection
The following vulnerability was exploited and fixed using the available php function mysql_real_escape_string()
Exploiting the sql injection
Fixing the SQL Injection vulnerability
After fixing the vulnerability
Final Vulnerability Scan Report
RIPS is a pretty smart tool to use for static php vulnerability analysis.
Concludes static code analysis with bug fixing example using RIPS tool.
Thank You...!














Nice blog. This blog provide useful information on static code analysis. I am looking for best static code analysis tools. Thanks for sharing
ReplyDeleteWhat is a sports betting point spread in sports to win?
ReplyDeleteA point spread means that your team scores exactly the same amount of points they would win if they had won their entire game. This means that your 토토 사이트 추천 team's